Security threats are ever increasing. As a result, many businesses are placing a greater emphasis on protecting their systems and data.
Below are eye-opening cyber security stats:
- 95% of cybersecurity breaches are caused by human error. (Cybint)
- 88% of organizations worldwide experienced spear phishing attempts in 2019. (Proofpoint)
- 68% of business leaders feel their cybersecurity risks are increasing. (Accenture)
- 45% of breaches featured hacking, 17% involved malware and 22% involved phishing. (Verizon)
Salesforce is the world’s leading CRM solution, and it stores billions of customers’ data. They take customer trust very seriously, and they provide various options to protect against unauthorized access.
Options for securely accessing Salesforce
Device Activation
Device Activation requires users to provide an additional authentication factor if they log in from an unrecognized browser or device, or if the user’s IP address is outside a trusted IP range. Supported verification methods for this feature include email and SMS text messages, as well as strong methods like Salesforce Authenticator, third-party TOTP authenticator apps, and security keys.
This will help in adding an additional layer of security, but it will only work if access is done using an unrecognized browser or device.
Single Sign On (SSO)
Single Sign On allows users to login in to Salesforce without entering their credentials. Instead, users sign in and authenticate through a third-party platform. This reduces risk by allowing users to use a single, strong password instead of memorizing several others. SSO is the best solution when used in conjunction with MFA (outlined below).
Multi-Factor Authentication (MFA)
Per Wikipedia:
Multi-factor authentication is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism: knowledge (something only the user knows), possession (something only the user has), and inherence (something only the user is). MFA protects the user from an unknown person trying to access their data such as personal ID details or financial assets.
MFA is one of the easiest and most effective tools for enhancing login security. By requiring two or more factors for authentications, it eliminates some of the most prevalent security threats.
Security risks MFA handles
- Phishing,Vishing,Smishing – These are cybercrimes in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.
- Spear phishing – Spear Phishing is a type of email attack in which a specific person or organization is targeted.
- Keyloggers – Keyloggers are a type of monitoring software designed to record keys pressed by a user. One of the oldest cyber threats, these keystroke loggers record the information you type into a website or application and send it back to a third party.
- Credential Stuffing – Credential stuffing is a type of cyberattack in which stolen account credentials, typically consisting of lists of usernames and/or email addresses and the corresponding passwords, are used to gain unauthorized access to user accounts through large-scale automated login requests directed against a web application
- Man in the middle attacks – A man in the middle (MITM) attack is a general term for when a perpetrator positions himself in a conversation between a user and an application—either to eavesdrop or to impersonate one of the parties, making it appear as if a normal exchange of information is underway.
Benefits of MFA
Stronger Authentication
It has been reported that over 80 percent of hacking-related breaches are caused by stolen or weak passwords. MFA allows the users to add multiple levels of security over the passwords, thus reducing the risk of unauthorized access.
Multiple Verification Methods
Salesforce has an order of precedence for verification methods when logging in with MFA:
- Salesforce Authenticator mobile app (available on the App Store or Google Play)
- Time-based one-time passcode (TOTP) authenticator apps, like Google Authenticator, Microsoft Authenticator, or Authy
- Security keys that support WebAuthn or U2F, such as Yubico’s YubiKey or Google’s Titan Security Key
- Built-in authenticators, such as Touch ID, Face ID, or Windows Hello
How Does MFA Work?
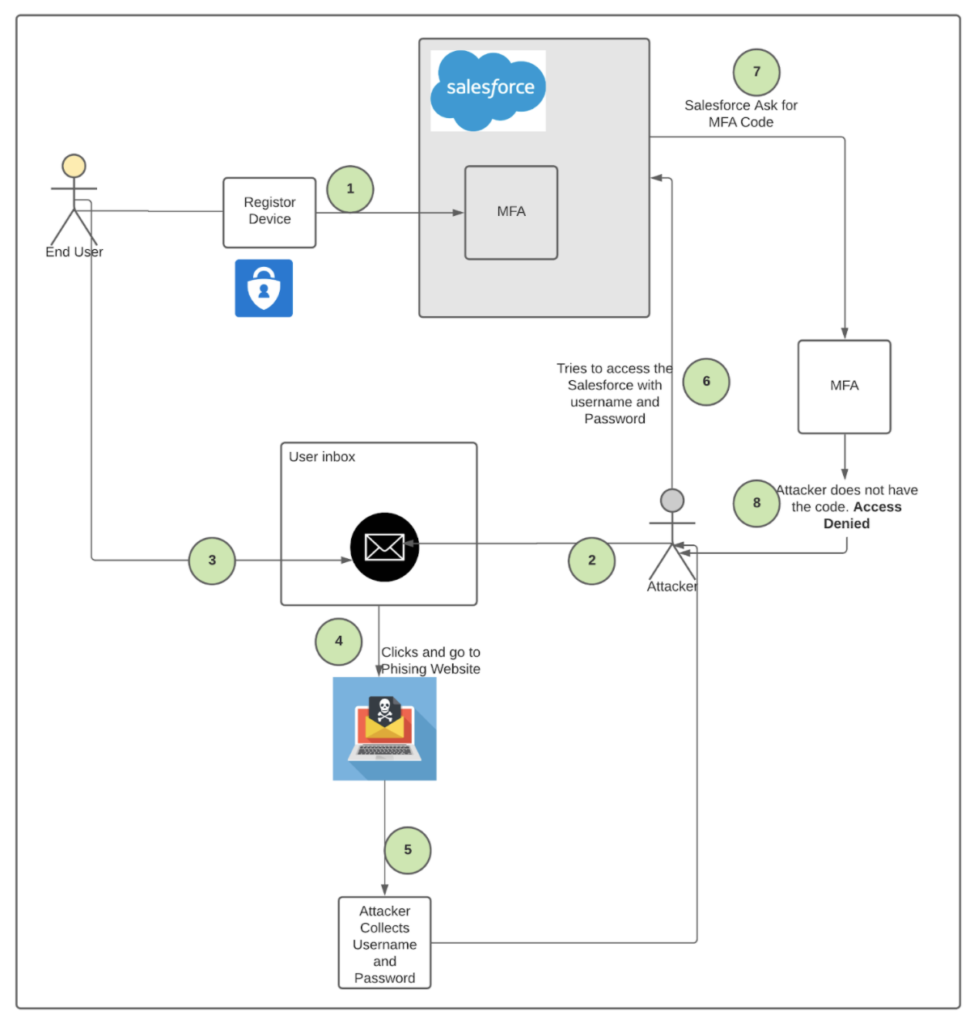
MFA won’t eliminate usernames and passwords. Instead, it adds another verification method to ensure that the proper users are logging in. Consider the following scenario:
- A Salesforce user has received a phishing email. Since the email seems to be trustworthy, he clicks a link and is brought to a fake website posing as Salesforce.
- The user enters his username and password, believing he’s simply logging in to his Salesforce account.
- The username and password that the user entered are sent back to the attacker. The attacker then tries to log in to Salesforce with these credentials.
- Since the user has activated MFA, Salesforce sends a push notification to his cell phone asking to verify. Since the attacker does not have access to the cell phone, the user’s account is still secure.
Subscribe to our blog for more technical information and industry news.








